Apache Webserver
Table of Contents
Todo
** Add explanations about .conf both **
Introduction
In this article, we will installed the Apache webserver. It is installed into a VM, which is running in Proxmox. For the installation of a VM in Proxmox, refer to Proxmox 6.2. The VM is based on Debian. Nevertheless this step-by-step guide is also valid for a native machine.
System configuration
User creation
Add a new user sphinx. It will be a system user and belong to the group www-data:
adduser --system sphinx --ingroup www-data
Change the password of the new user:
passwd sphinx
Webserver installation
Under a Debian OS, Apache server installation is simple as:
sudo apt-get install apache2
Apache configuration
For safety reasons, comment all following lines in the file /etc/apache2/apache2.conf:
#<Directory /usr/share>
# AllowOverride None
# Require all granted
#</Directory>
#<Directory /var/www/>
# Options Indexes FollowSymLinks
# AllowOverride None
# Require all granted
#</Directory>
In order to forward http requests toward https server, activate the rewrite module:
sudo a2enmod rewrite
In order to communicate with Apache server in https mode, a certificate will be created. It allows a secure communication between client and server. OpenSSL will be used to create it. It should be already installed on the system. Create new certificate:
sudo openssl req -x509 -nodes -days 365 -newkey rsa:2048 -keyout /etc/ssl/private/sphinx-selfsigned.key
-out /etc/ssl/private/sphinx-selfsigned.crt
Note
A certificate must be used for a communication in https mode. A selfsigned certificate will be created on the server. But this certificate is not signed by an authority. This is why a warning will be displayed on client browser, only for LAN local access. For access from WAN side, a certificate signed by Let’s Encrypt is used by pfSense. Thus, no warning will be displayed.
Web site configuration
http mode
Add an Apache configuration file /etc/apache2/site-available/sphinx.conf:
<VirtualHost *:80>
ServerName sphinx.legibus.fr
ServerAlias 192.168.1.9
DocumentRoot "/rep/to/the/site/web/"
ErrorLog ${APACHE_LOG_DIR}/error.log
CustomLog ${APACHE_LOG_DIR}/access.log combined
Protocols h2 http/1.1
<IfModule mod_rewrite.c>
Redirect permanent / https://sphinx.legibus.fr/
</IfModule>
Header set X-Robots-Tag "noindex, noarchive, nofollow"
<Directory "/rep/to/the/site/web/">
Require all denied
# AllowOverride none et AllowOverrideList none to ignore access to .htaccess
AllowOverride AuthConfig
AllowOverrideList none
Options -Indexes +FollowSymlinks +Includes +MultiViews
Order allow,deny
Allow from all
Header set X-Robots-Tag "noindex, noarchive, nofollow"
SetEnv HOME /rep/to/the/site/web/
SetEnv HTTP_HOME /rep/to/the/site/web/
Satisfy Any
</Directory>
<Directory /rep/to/the/site/web/blog/>
#blog et work to be protected
AuthName "Restricted area !"
AuthBasicProvider file
AuthUserFile /usr/local/apache/passwd/passwords
AuthGroupFile /usr/local/apache/passwd/groups
Require user web
</Directory>
</VirtualHost>
Pour le second pointfefeaf/
Then, enable the configuration:
sudo a2ensite sphinx.conf
Finally, reload the Apache server:
sudo systemctl reload apache2
https mode
Add an Apache configuration /etc/apache2/site-available/sphinx-ssl.conf:
<IfModule mod_ssl.c>
<VirtualHost *:443>
ServerName sphinx.legibus.fr
ServerAlias 192.168.1.9
DocumentRoot "/rep/to/the/site/web/"
ErrorLog ${APACHE_LOG_DIR}/error.log
CustomLog ${APACHE_LOG_DIR}/access.log combined
SSLEngine on
SSLCertificateFile /path/to/certificate/sphinx-selfsigned.crt
SSLCertificateKeyFile /path/to/certificate/sphinx-selfsigned.key
Protocols h2 http/1.1
Header set X-Robots-Tag "noindex, noarchive, nofollow"
<Directory "/rep/to/the/site/web/">
Require all denied
# AllowOverride none et AllowOverrideList none pour ignorer l'acces à .htaccess
AllowOverride none
AllowOverrideList none
Options -Indexes +FollowSymlinks +Includes
Order allow,deny
Allow from all
SetEnv HOME /rep/to/the/site/web/
SetEnv HTTP_HOME /rep/to/the/site/web/
Satisfy Any
</Directory>
<Directory /rep/to/the/site/web/blog/>
#blog et work to be protected
AuthName "Restricted area !"
AuthBasicProvider file
AuthUserFile /usr/local/apache/passwd/passwords
AuthGroupFile /usr/local/apache/passwd/groups
Require user web
</Directory>
</VirtualHost>
</IfModule>
SSLProtocol all -SSLv3 -TLSv1 -TLSv1.1
SSLHonorCipherOrder off
SSLCipherSuite ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:
ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:
ECDHE-RSA-CHACHA20-POLY1305:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384
SSLSessionTickets off
SSLUseStapling On
SSLStaplingCache "shmcb:logs/ssl_stapling(32768)"
Then, enable the configuration:
sudo a2ensite sphinx-ssl.conf
Finally, reload the Apache server:
sudo systemctl reload apache2
Firewall configuration
In order to access to the webserver from the WAN, the Squid Reverse Proxy of pfsense is used. Open menu :
Fig. 50 Webserver list
Add a new webserver with the local IP and the port to reach it (ie with port 80 (http) see Fig. 51):
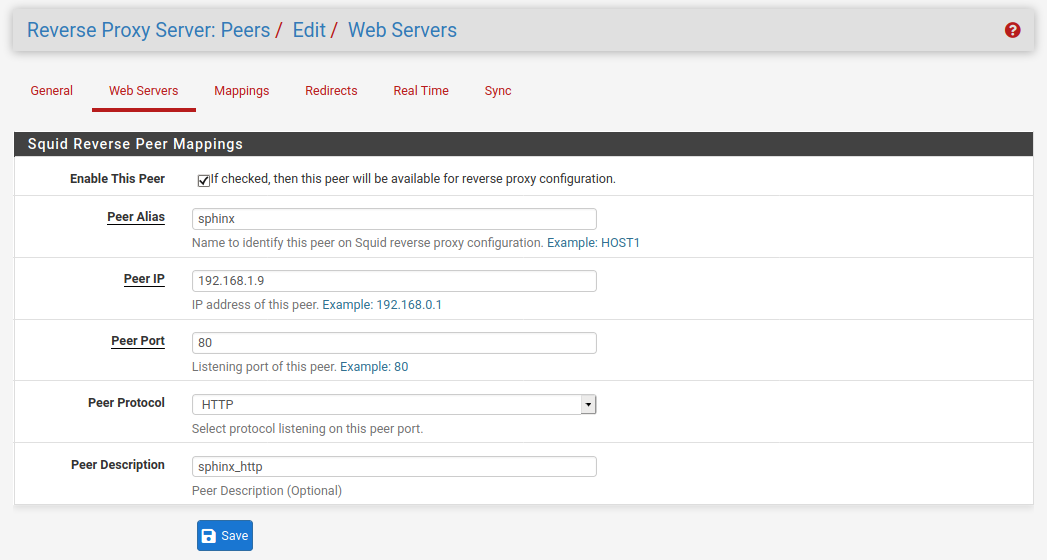
Fig. 51 Webserver mapping
Note
Make the same with the same local IP but replace port 80 with the port 443 (https).
It is time to check if the webserver is reachable from the WAN. If the Apache default web page can be read (see Fig. 52):
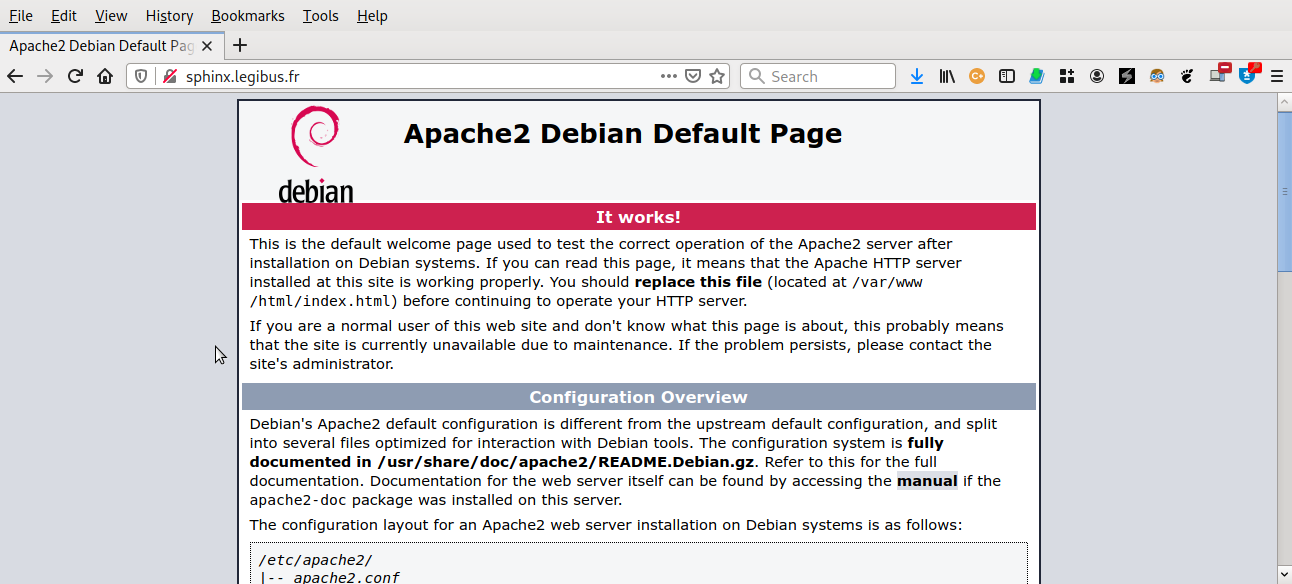
Fig. 52 Apache default web page
Final configuration
Once the default Web site is available, it can be disable:
sudo a2dissite 000-default.conf
And all html files should be placed into the root of the server (“/rep/to/the/site/web/” in the example).
Bibliography
- Date
2021-04-28 22:00
- Tags
pfsense, webserver, computer, virtual machine, apache, certificate
- Authors
Gibus